An Introduction to Webb’s Systems 2: Cross-Chain Zero-Knowledge Identity Systems
Webb’s system for cross-chain identity systems
This is the second blog post in a three part introduction series to Webb’s systems. Part 1 described Webb’s system for cross-chain asset transfers, part 2 (this post) describes Webb’s system for cross-chain identity systems, and part 3 will combine parts 1 and 2 and describe an identity-based cross-chain asset transfer system.
Semaphore Protocol Overview
Semaphore Protocol allows users to prove membership in a group via a zero-knowledge proof. An example application where Semaphore is useful is anonymous voting: 1) whitelisted voters are allowed to register as part of a Semaphore group, 2) later on they can submit a vote by proving they are part of the group, without revealing their exact identity. The anonymity set size is the size of the Semaphore group.
Semaphore Technical Details
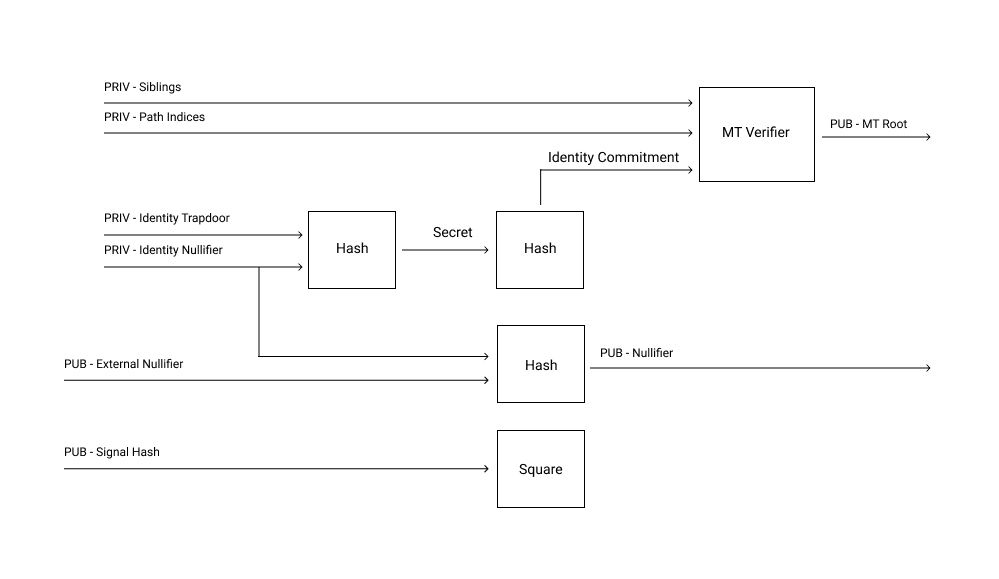
- A Semaphore identity consists of two values, an
identity trapdoorand anidentity nullifier. These values can either be randomly generated or created deterministically. - The
identity secretis thePoseidon(identity trapdoor, identity nullifier). - The
identity commitmentisPoseidon(identity secret)and is the user’s publicly visible anonymous identity. - Each Semaphore group has a corresponding Merkle tree. When a user registers as part of a group, their
identity commitmentis added to the group’s Merkle tree. - Now, suppose a user wants to cast an anonymous vote. To achieve this, they will prove in zero-knowledge that they know an
identity nullifierandidentity trapdoorcorresponding to anidentity commitmentin the Semaphore group’s Merkle tree. See the circuit for this zero-knowledge proof here. - One question remains to be solved: how can we prevent the same user from casting multiple anonymous votes.
- In Semaphore, this is achieved via the
external nullifier. Each poll has anexternal nullifierassociated with it. When a user casts a vote a correspondingnullifier hash = Poseidon(external nullifier, internal nullifier)is exposed. If a user ever tries to vote in the same poll again, the nullifier hash will be the same and it is easily detected that the user is trying to double-vote.
See Semaphore’s diagram below for an architecture of the zero-knowledge proof system:
Extending to Semaphore to be Cross-Chain
Our cross-chain Semaphore Protocol allows a user to register as part of a Semaphore group on one chain and submit a zero-knowledge proof of group membership on another chain. The mechanism we use to do this is very similar to the mechanism for cross-chain asset transfers in the previous blog post. For each Semaphore group, there is an associated linked Merkle tree on each blockchain. Suppose a user registers on chain A and wants to anonymously prove membership on chain B. Since chain B stores the Merkle root of the linked Merkle tree on chain A, a Merkle proof can be submitted in zero-knowledge against this root.
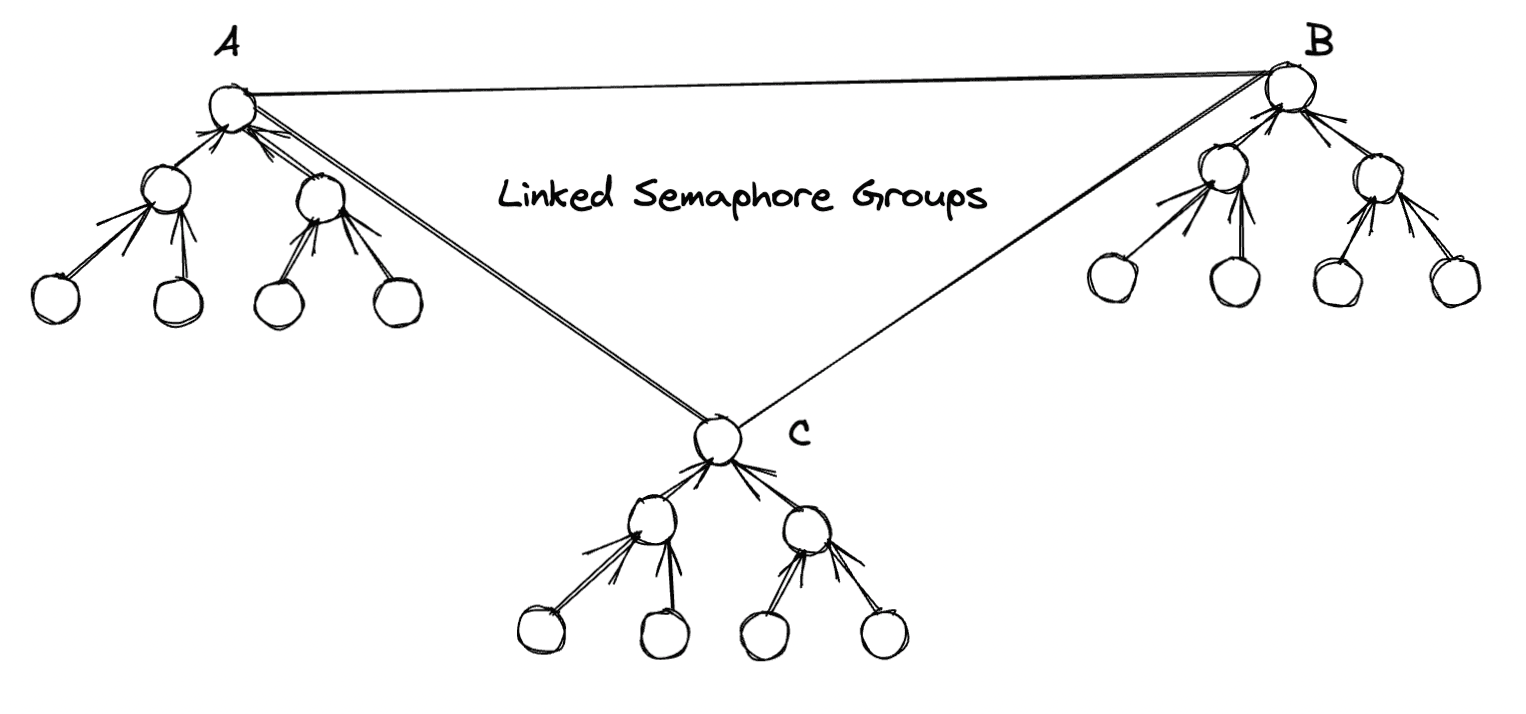
Why cross-chain Semaphore?
What is the purpose of a cross-chain Semaphore system? Suppose a bridge for transferring assets across blockchains is only available to members registered in a Semaphore group. That is a user can deposit/withdraw on a blockchain if and only if it proves membership in a particular Semaphore group on that blockchain. This leads to an unwieldy user experience. For every blockchain the user interacts with they have to register as part of the corresponding Semaphore group on that blo/ckchain. What if we could create a system of bridged Semaphore groups wherein a user can prove on one blockchain that it is part of the Semaphore group on another blockchain. This implies the user only has to register in a Semaphore group on one blockchain yielding a much improved user experience. This is exactly what Webb’s cross-chain zero-knowledge identity system allows for.
And if nothing else, cross-chain Semaphore allows us to increase the size of the anonymity set to include the sum of users across multiple blockchains.
Applications that can be built with cross-chain Semaphore
Our work is completely open source and extensible. The relevant repo is: https://github.com/webb-tools/semaphore-anchor/. Here are some ideas for apps that can be built with our cross-chain Semaphore infrastructure: cross-chain anonymous voting, cross-chain anonymous whistleblowing, cross-chain anonymous forum posting, anonymous login and authenticate, etc.
Anonymous voting
Cross-chain anonymous voting allows users to anonymously cast their vote without revealing their exact identity. This application can be used for many scenarios, such as elections, surveys, polls, and other forms of anonymous voting. This type of voting is useful for organizations that want to ensure the privacy of their members and for individuals who want to remain anonymous. It is also useful for governments, businesses, and other organizations that need to collect anonymous feedback from their members or customers.
Forum posting
Anonymous forum posting is a powerful tool that can be used to allow users to participate in a discussion without revealing their exact identity. This can be achieved using a cross-chain anonymous identity system like Webb’s Semaphore extension. This system allows users to prove membership in a group via a zero-knowledge proof, and then use that proof to post anonymously on a forum from any blockchain. The benefits of this system are that users can remain anonymous while participating in a discussion and can also increase the anonymity set size, allowing for more privacy and security. This is useful for organizations that need to collect anonymous feedback from their community members.
Zero-knowledge based login
Webb's interoperable Semaphore Protocol can be used to create an anonymous login system. This system allows a user to prove membership in a Semaphore group without revealing their exact identity. This can be used to authenticate users in a secure and private way.
Anonymous login systems are useful for a variety of applications such as financial services, e-commerce, and social applications. Anonymous login systems provide users with a secure and private way to authenticate their identity without revealing their personal information. This type of system is beneficial for users who value their privacy and want to protect their data.



